This is an offer for all SME that utilizes Microsoft Entra ID as their primary Identity provider and that want to strengthen their IT Security posture.
Buy an IT Security package

We guarantee you will not be the hackers’ preferred victim: an easy target!
You don’t have to outrun the bear, just the person next to you.
This package establishes fundamental security controls tailored for your business needs.
From DKK 48.500
IT Security package content
- Security analysis of your specific Microsoft environment (see Microsoft licenses)
- Overall assessment of your IT footprint and your key assets
- Security awareness training
- Implementation of low hanging fruits
- Prioritized roadmap with IT Security initiatives

Gain a competitive advantage
Many companies have enough security controls at their disposal to be a difficult target but they simply lack security awareness training and they haven’t configured the security controls to counter efficiently a cyberattack.
This stand-alone IT Security package is perfect for SME that are not big enough to have their own IT Security department but are reliant on IT to support their main business objectives.
IT Security is not a cost. Many see IT Security initiatives as solely risk reducing where the value is not tangible but that’s not correct. Here is a list of IT Security initiatives examples that add business value and simultaneously increase the IT security posture:
- Passwordless Authentication: Enhances security by reducing the risk of password-related attacks and streamlines the user authentication process, leading to quicker access to systems and applications for employees and customers.
- Single Sign-On (SSO): Adopting SSO solutions allows users to authenticate once to access multiple applications and resources, eliminating the need to remember and enter multiple passwords and shortens lead times for accessing critical resources and applications.
- Automated Identity and Access Management (IAM): Implementing automated IAM solutions for user provisioning, deprovisioning, and access management streamlines the onboarding and offboarding processes for employees, contractors, and partners and thereby reducing manual intervention and administrative overhead.
- Secure DevOps Practices: Integrating security into the DevOps pipeline enables organizations to identify and remediate security vulnerabilities early in the software development lifecycle. By automating security testing and compliance checks, Secure DevOps practices accelerate the delivery of secure and reliable software, leading to shorter lead times for software releases and updates.
- Zero Trust Network Access (ZTNA): Adopting ZTNA solutions allows organizations to enforce granular access controls based on user identity, device posture, and contextual factors, regardless of network location. By eliminating the need for traditional VPNs and perimeter-based security controls, ZTNA solutions enable secure and seamless access to resources and applications from any location or device, reducing lead times for remote work and distributed collaboration.
- Privacy Compliance Program: Implementing robust privacy compliance measures not only ensures regulatory compliance but also enhances customer trust and loyalty, potentially leading to increased sales and brand reputation.
- Cybersecurity Awareness Training: Educating employees about cybersecurity best practices not only reduces the risk of insider threats and human errors but also cultivates a security-conscious culture, which can be marketed as a competitive advantage to clients and partners.
- Vendor Security Assessment Program: Conducting thorough security assessments of vendors and third-party partners mitigates supply chain risks and assures customers of the security and integrity of products and services, thereby enhancing brand credibility and marketability.
- Incident Response and Business Continuity Planning: Establishing robust incident response and business continuity plans minimizes downtime and disruption in the event of a security incident, safeguarding revenue streams and maintaining customer trust and satisfaction.
- Security-by-Design Services: Offering security-by-design services to clients ensures that security is integrated into products and services from the outset, providing a competitive edge in markets where security is a key concern for customers.
- Secure Cloud Adoption Strategy: Developing a secure cloud adoption strategy enables businesses to leverage the scalability and cost-efficiency of cloud services while effectively managing security risks, potentially increasing operational efficiency and competitiveness.
- Data Encryption and Protection: Employing strong encryption and data protection measures not only safeguards sensitive information from unauthorized access but also demonstrates a commitment to data privacy and security, which can be leveraged for marketing purposes.
- Security Metrics and Reporting: Establishing key security metrics and reporting mechanisms allows businesses to track and communicate their security posture effectively, instilling confidence in customers and stakeholders and potentially attracting new business opportunities.
Are you using Microsoft Entra ID (formerly Azure AD)?
At Ganc Consulting, the aim is to significantly improve your company’s IT Security posture.
This is done by training the staff, configuring systems and help with creating an IT security roadmap with prioritized initiatives so you know what you should do next.

To maintain affordability, it is required that your company utilizes Microsoft Entra ID as a primary cloud Identity Provider.
Microsoft licenses
What is included in the IT Security package will depend on what capabilities there are at disposal.
The following table lists all features available based on license type.
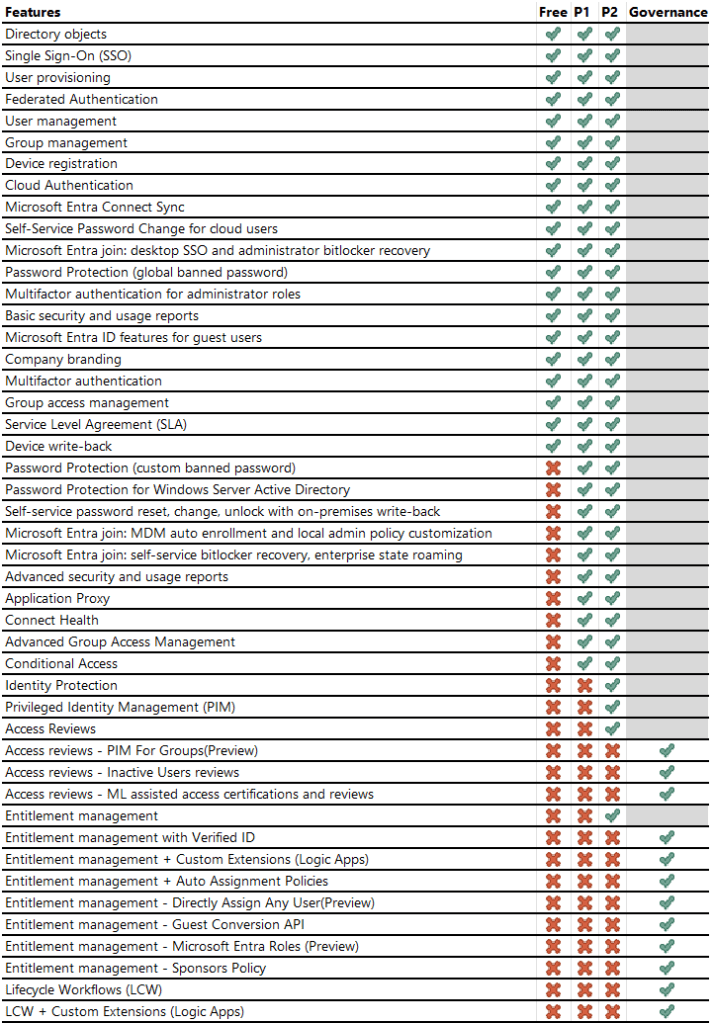
- Free: Microsoft cloud subscriptions such as Microsoft Azure, Microsoft 365, Microsoft Dynamics 365, Microsoft Intune, Microsoft Power Platform
- P1: standalone or included with Microsoft 365 E3 for enterprise customers and Microsoft 365 Business Premium
- P2: standalone or included with Microsoft 365 E5 for enterprise customers
- Governance: MS Entra ID Governance add-on license for Microsoft Entra ID P1 and P2 customers. Special pricing is available for Microsoft Entra P2 customers.
Small- and Medium-Sized Enterprises
According to the Danish Agency for Digital Government analysis from 2023: 35% of every SME has insufficient IT Security posture compared with its risk profile. This makes them vulnerable to all sorts of cyberattacks i.e. Ransomware, DDoS, Data leakage and more.
Don’t be part of the statistics, buy your IT Security package today and show your customers, employees, collaboration partners and even your insurance company that you take IT Security seriously.
Want to find out more? Let’s schedule a non-binding meeting.
